Quantum key distribution devices:
How to make them and how to break them
PhD Thesis Defense
Sarah Kaiser
Institute for Quantum Computing
Classical infrastructure is already horribly compromised.
Attacks on classical key exchange will only get worse.
At least many people are Shor...
Potentially Secure Key Exchange
Post-quantum cryptography
Quantum key distribution
Why don't we all have quantum keys?
Distance/Loss: $\approx 300$ km
Hardware developments
Realistic device security models
One approach:
QKD receiver satellite
How to make them and how to break them
Distance →
Modeling for airborne QKDHardware →
Robust quantum optical componentsSecurity models →
Novel laser damage attack on commercial system
Distance:
Getting to space is costly
Test platform candidates


Model risk assessment
GOAL:
establish a QKD link with parameters representative of a modeled, night satellite pass.METRICS:
Link time [s] → $\approx 250$
angular velocity [˚/s] → {0.7,1.2}
Raw key rate [kHz] → $\approx 1$
Stratospheric balloons
Timmins
![Timmins]()
Visual assessment
![Modeled]()
| Flight # | Timmins | Visual | Altitude |
| 1 | ❌ | ❌ | ❌ |
| 2 | ❗ | ➖ | ➖ |
| 3 | ❗ | ➖ | ✔ |
| 4 | ❌ | ➖ | ✔ |
| 5 | ❌ | ➖ | ✔ |
| 6 | ❌ | ❌ | ❌ |
| 7 | ❌ | ❌ | ✔ |
| ❌ | Fail (< 5 min) | ||
| ❗ | High risk (< 30 min) | ||
| ➖ | Moderate risk (< 60 min) | ||
| ✔ | Low risk (> 60 min) | ||
Plane constraints

Comms test flights
Infrastructure:
robust devices up to the task
QKD receiver satellite
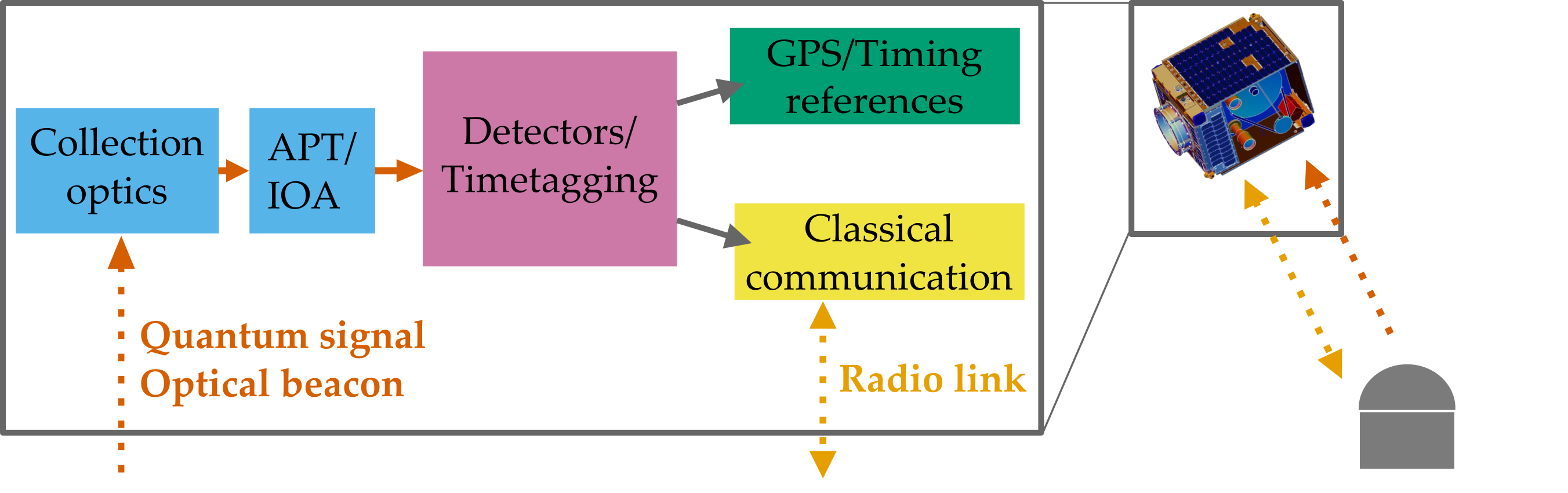
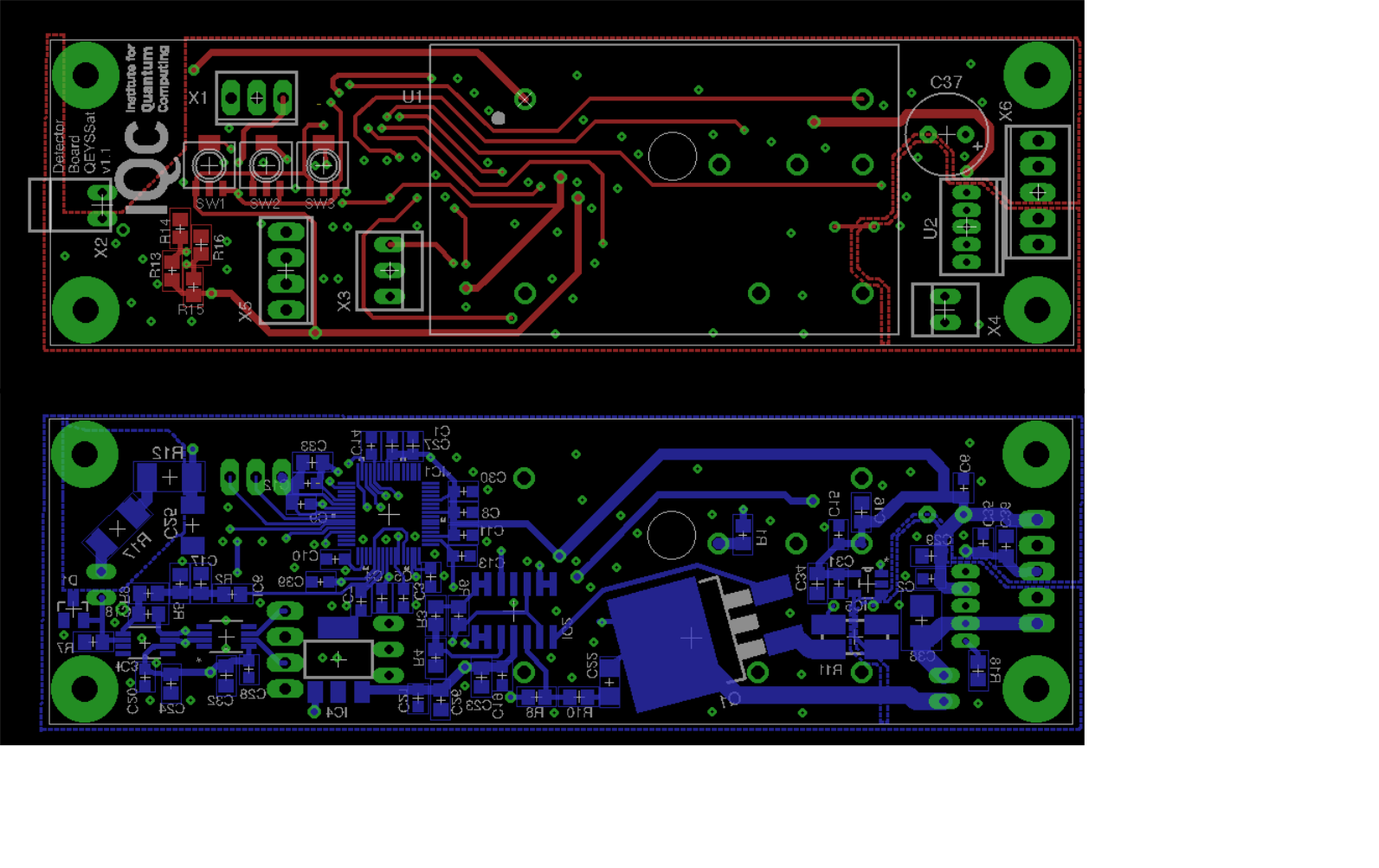
Single photon detector unit

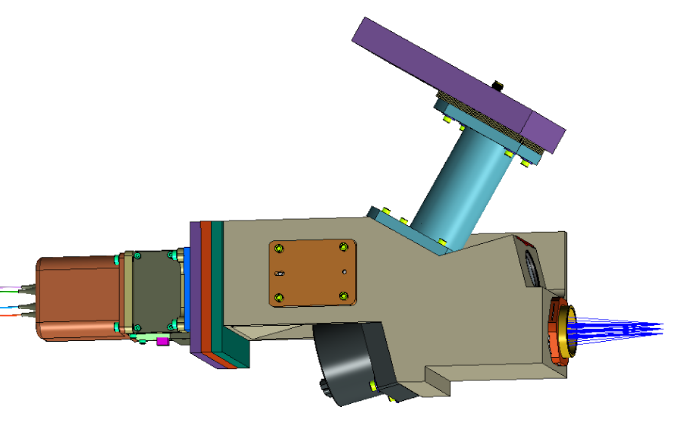
Integrated optical assembly (IOA)
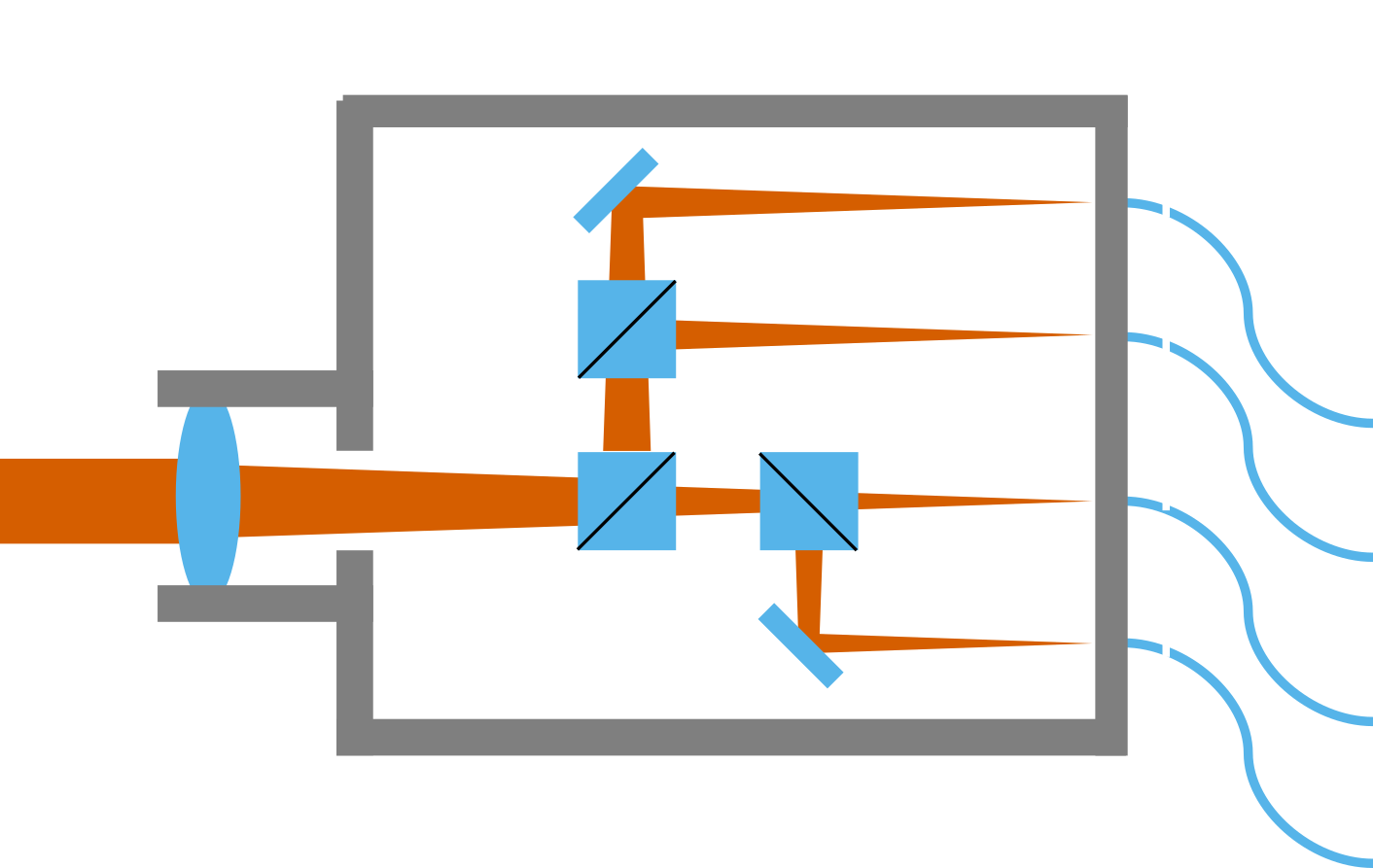
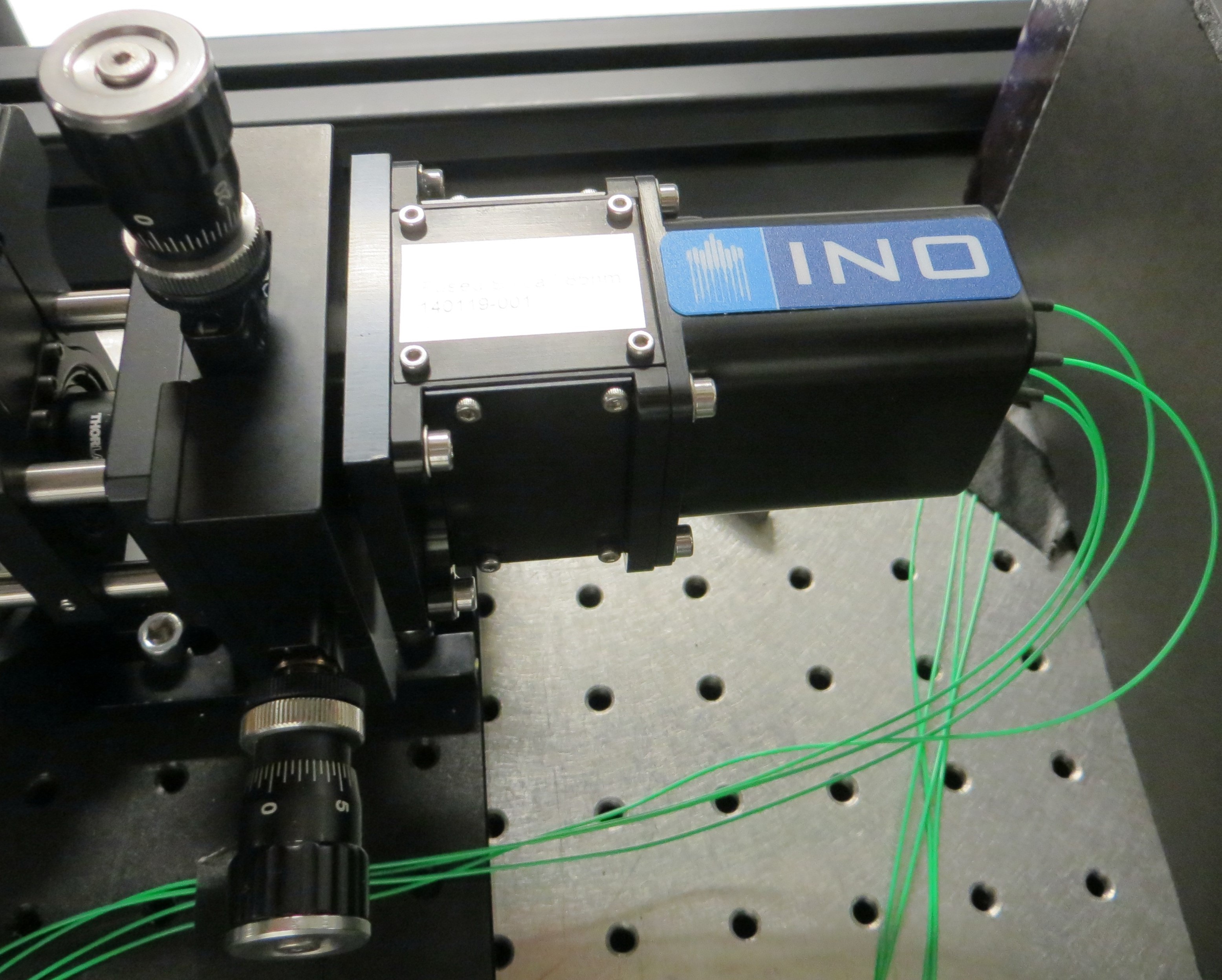
Acquisition pointing and tracking (APT)
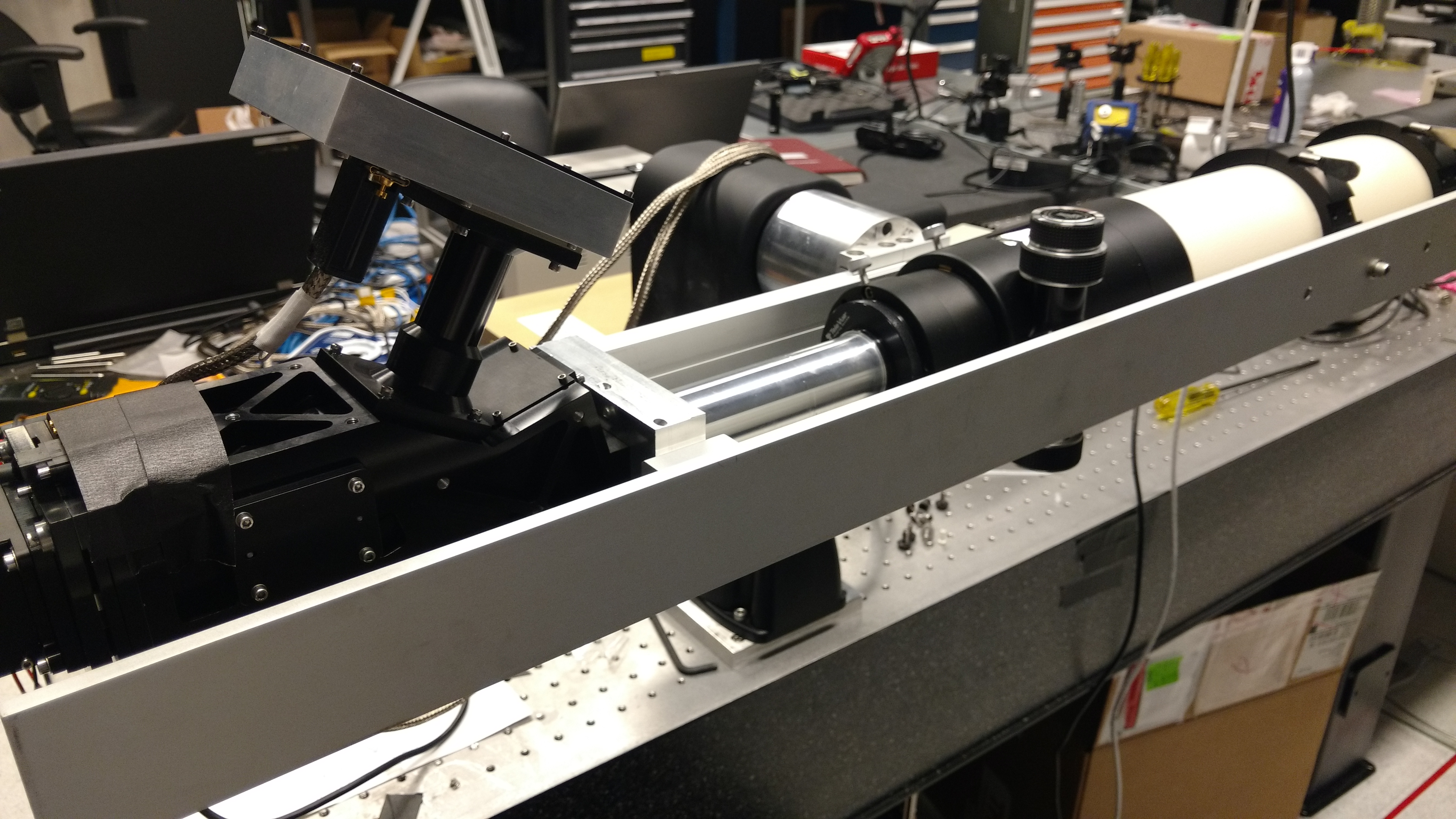
QBER
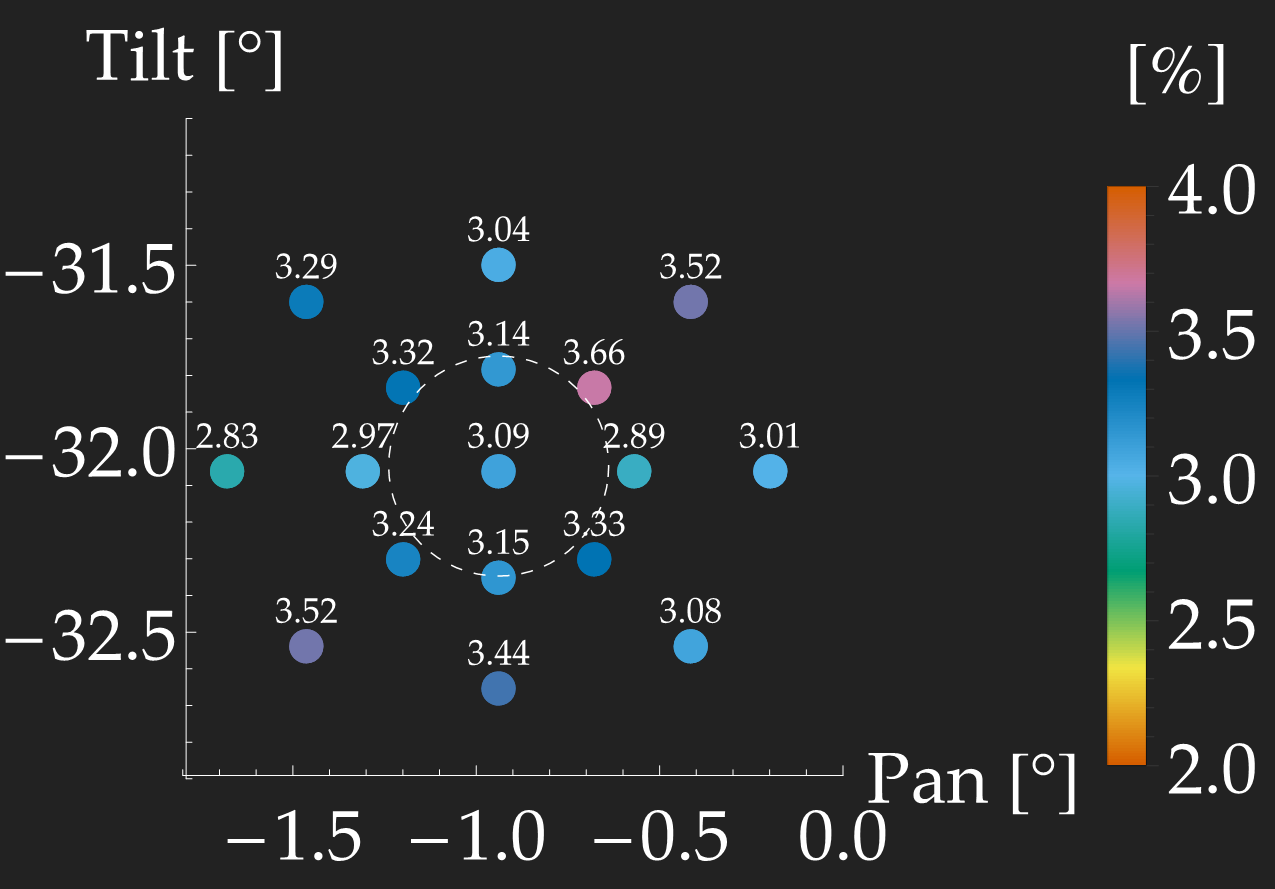
Security:
Functionality $\neq$ security
No demonstrated successful countermeasures!
How we made them and how I broke them
Distance →
Modeling for airborne QKDHardware →
Robust quantum optical componentsSecurity models →
Novel laser damage attack on commercial system